DFOH is a system designed to detect forged-origin hijacks across the entire Internet.
Forged-origin hijacks are typically malicious BGP hijacks where attackers manipulate
the AS path of BGP messages to make them appear as legitimate routing updates.
DFOH is particularly useful because the proposed BGP extensions for cryptographically verifying the validity
of AS paths (e.g., BGPSec or ASPA) are challenging to deploy widely.
With DFOH, operators can quickly and confidently determine when their traffic is being hijacked.
Watch our APRICOT'24 presentation
or read our NSDI'24 paper.
Network operators can quickly be informed when their traffic is possibly being hijacked and take proper countermeasures if necessary. Watch the suspicious cases
detected in real-time
Researchers and network operators can use this data to pinpoint hackers and blocklist them or to find misconfigurations that lead to bogus BGP hijacks. Watch the suspicious cases
detected in the past
Why detecting forged-origin BGP hijacks matters
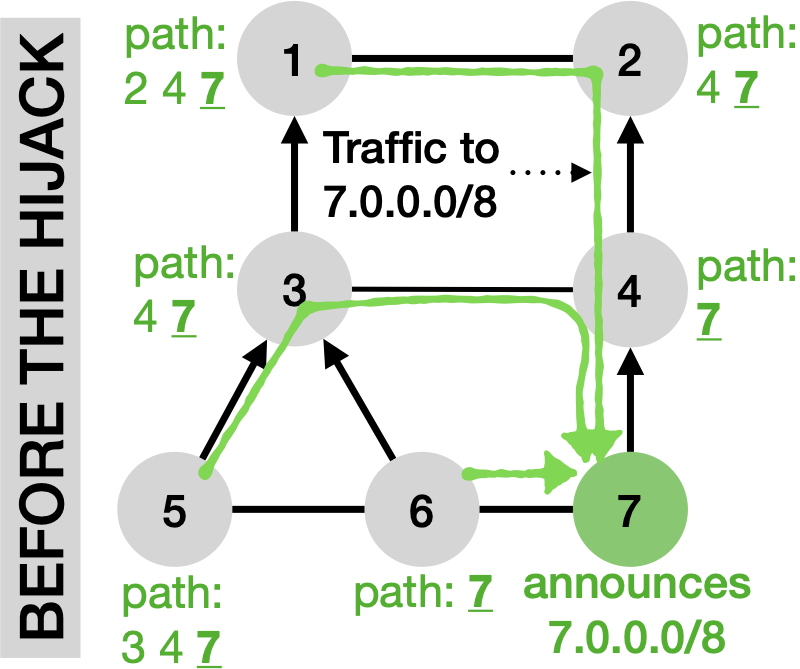
However, forged-origin hijacks have been left uncovered by such solutions—despite these attacks being actively used in the wild. Consider the scenario on the left, which depicts an AS-level topology with seven ASes connected using peer-2-peer or customer-2-provider business relationships. AS7 announces the IP prefix 7.0.0.0/8 and traffic to this prefix is highlighted in green.
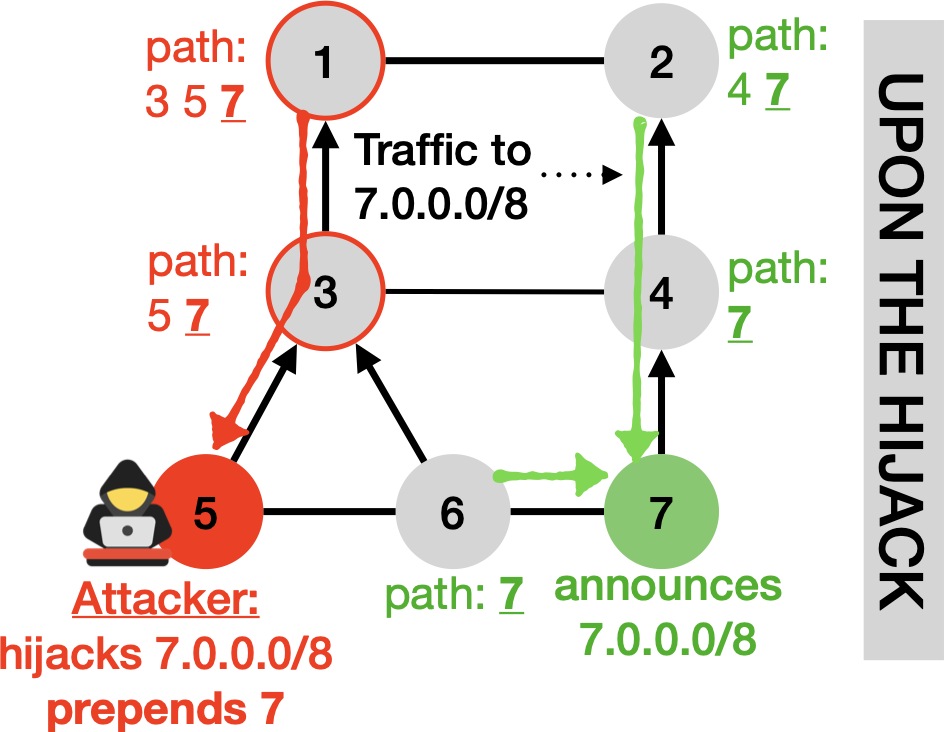
Imagine now that AS5 is a hacker and announces a route for prefix 7.0.0.0/8 and prepend AS7 in the AS path. Thus, the hijacked route appears legitimate from BGP standpoint, preventing the cryptographically-based path origin verification techniques (RPKI-ROV) to detect this fake route. AS1 and AS3 will divert traffic to 7.0.0.0/8 to the hacker (red arrows), making the attack successful. This attack is called a forged-origin BGP hijack and is actively used by hackers.
What you can expect from DFOH
DFOH relies on an new algorithm that detects fake AS links in AS paths in a probabilistic fashion (using artificial intelligence) as opposed to cryptographically based solutions such as BGPSec. Detecting fake AS links is useful as they are a strong sign of a forged-origin hijack. The advantage of DFOH against the cryptographically based counterparts is that it is easy to deploy. The disadvantage is that there are false positives and false negatives.
We evaluate DFOH on forged-origin hijacks that we artificially created and found that it pinpoints 90.9% of the hijacks and only incorrectly classifies a new legitimate link as suspicious in 1.9% of the cases.
We ensured that our artificial forged-origin hijacks on which we tested DFOH cover a wide range of attack scenarios. We found that DFOH is accurate regardless of who is the victim and who is the attacker.
DFOH is a practical tool for network operators
The figure above illustrates the number of suspicious cases reported by
DFOH when deployed on the real Internet.
Overall, DFOH reduces the number of suspicious cases by 13.1 times compared
to existing techniques that simply report every new AS.
In July 2022, the highest number of suspicious cases detected by DFOH for a given AS was 15, averaging one every two days.
The vast majority of ASes (99.8%) were involved in zero or one suspicious case during the month.
Consequently, network operators can easily investigate each suspicious case detected by DFOH
that involves their AS and quickly implement countermeasures if necessary.